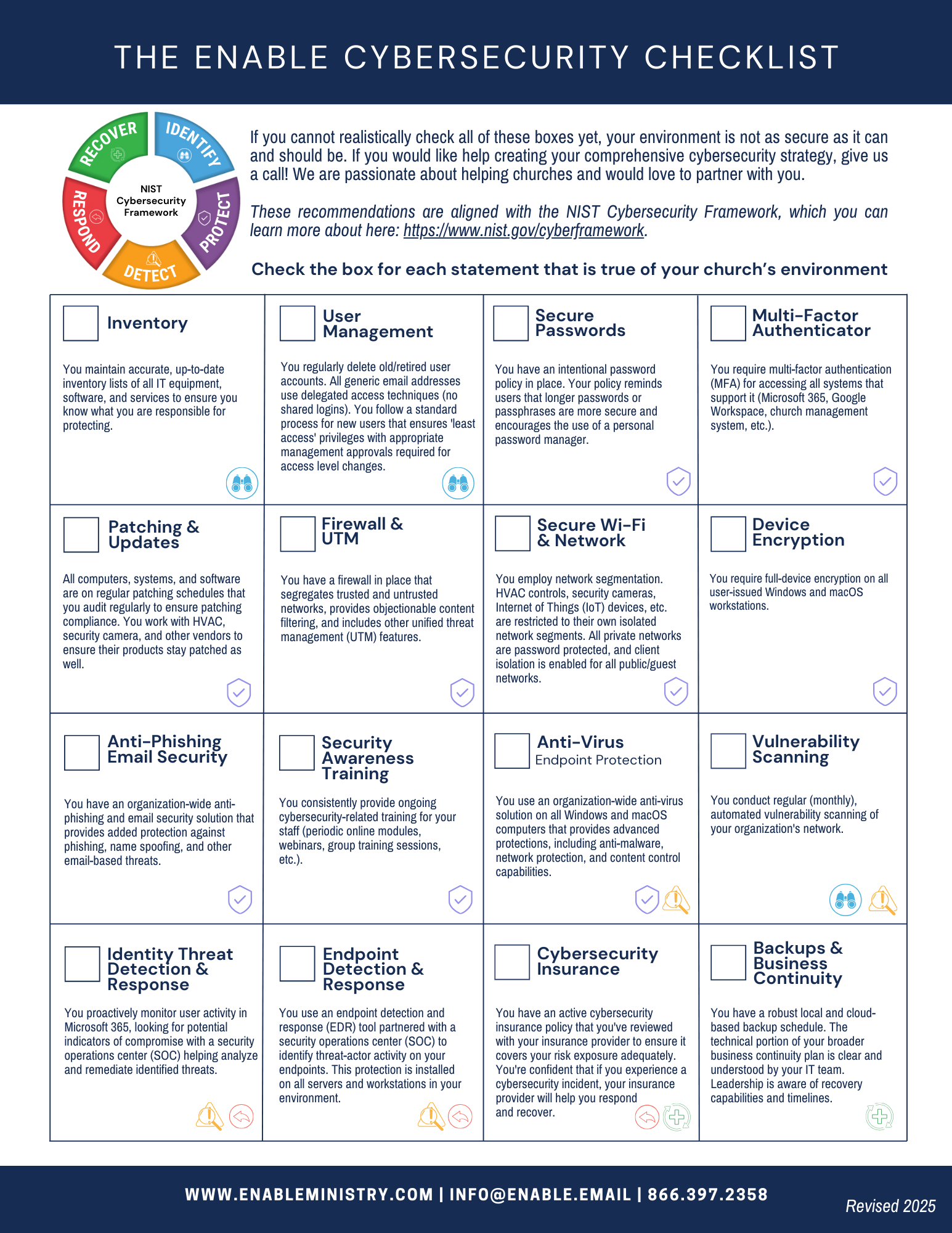
The items on this checklist are a great starting point for measuring your church’s level of security, but the checklist is not a guarantee of protection. Instead, it is a guide to help move you in the right direction. In the cybersecurity world, things are constantly changing; new threats arise daily. Implementing all these checklist items is a vital first step in the right direction, but you must continually be vigilant, stay aware, and regularly educate yourself and your staff.

Defend Your Data: The Enable Cybersecurity Checklist
Cybersecurity is a crucial issue that requires the attention of anyone charged with leadership of a church, ministry, school, business, or any other type of organization. The reality is that threats and risks associated with cyberattacks are rising exponentially. While it may not seem evident initially, churches are a popular target of cybercriminals. Why are churches targets? First, churches are attractive targets because they often maintain members' valuable personal and financial information. Second, most churches are not prepared to protect themselves against cybercriminals who seek to do them harm.
Increasingly, church leaders must prioritize implementing comprehensive, effective cybersecurity plans, procedures, and training. These "non-negotiables" are for anyone involved in a technology-enabled ministry environment. While most leaders understand their responsibility in this area, many do not know where to begin planning their strategy and often approach the topic with confusion.
At Enable, we work with these leaders daily. Our clients regularly ask us the same two introductory questions:
"What steps should I be taking to protect our church?" and “What should I tackle first?"
We have created the Enable Cybersecurity Checklist to help leaders assess the security level of their church's technology environment. This checklist provides a roadmap for implementing vitally important security measures within your specific church environment.
1. Inventory
To protect something, you must be able to account for it. It’s vitally important that you have a complete inventory of all network and computer equipment owned by your organization, and that you are cognizant of every place where data is stored (local servers, workstations, cloud services, etc.). You can’t protect systems or data that you aren’t aware of.
2. User management
Ensuring that only current, active employees have access to your computers and network environment is of vital importance. You must also limit employee and volunteer access to only the systems and data needed for them to perform their job functions. You must regularly delete old user accounts and follow a standard process for new user setups that ensures 'least access' privileges with appropriate management approvals required for access level changes.
3. Secure passwords
Accounts with weak, easy-to-guess, or reused passwords are “low-hanging fruit” for cybercriminals. A password policy that requires strong, unique passwords and encourages using a password manager is one of the most crucial security measures an organization can take.
4. Multi-Factor Authentication (MFA)
The goal of multi-factor authentication is to verify identity and ensure that the person logging into an account genuinely is the person they claim to be. MFA is necessary because passwords alone do not deter security breaches and cybercrime. On top of secure passwords, MFA provides a second layer of protection and security. It strengthens security during login and is an accessible, helpful, and easily implemented solution.
5. Patching/updates
One of the most valuable and straightforward ways to keep your technology environment secure is to stay up-to-date with software and firmware patches. Patching is simple; it just takes disciplined, consistent attention. In most successful cyber breaches, hackers obtain access to data or systems via well-known software bugs for which patches already exist but which IT administrators have never applied!
6. Firewall with Unified Threat Management (UTM)
Basic firewalls have been a "must-have" for years, but rising security threats call for firewall platforms with enhanced protection. Today's firewall platforms include UTM features such as Intrusion Detection and Prevention, Gateway antivirus, Geo-IP filtering, and objectionable content filtering. A basic firewall doesn't do enough to protect you without these advanced capabilities.
7. Secure Wi-Fi & network
When it comes to Wi-Fi, there is no one-size-fits-all solution. Still, church IT staff must properly segment/isolate traffic across the church's wired and wireless networks. It must encrypt all sensitive Wi-Fi traffic to the highest available standards. A secure wireless environment will utilize strong user authentication for staff network access, will have a separate guest network with client isolation enabled, and should work in tandem with a UTM firewall solution as described above. Additionally, Internet of Things (IoT) devices like building automation controls (e.g., HVAC, door access controls, lighting systems, security cameras, etc.) should each have their own network segments, isolating each system type from talking with other network devices.
8. Device Encryption
Disk encryption is vital to protecting your systems and thwarting those determined to misappropriate your data. It enables you to store information on your technology devices in a state that an unauthorized user cannot easily access. So, if a cyber thief physically steals your computer, it will be difficult for him to read and utilize this data.
9. Anti-phishing/email security
Email is, far and away, the preferred method for hackers who desire to steal information, money, and access. We recommend implementing a system that focuses explicitly on stopping phishing attempts and goes beyond the traditional spam filtering provided by your email provider. This one move is a significant first step in protecting against vulnerability in this area. Solutions that provide much more protection and power than those supplied with your email hosting platform are available and affordable. However, anti-phishing solutions are not enough in and of themselves. Fraudulent email schemes are becoming increasingly more sophisticated, and we must train our staff members to recognize and avoid common email attacks.
10. Security awareness training
The most vulnerable link in all churches' cybersecurity prevention efforts is the human element – the staff. The staff? Why? The reason is almost always because the staff has not received adequate training to recognize security threats, how these threats may manifest, and how to respond to an attack. As humans, staff members can and do make mistakes! They trust fake identities, fall for alluring "clickbait," and can become entangled in many other sneaky cybercriminal schemes. The best protection for cyberthreats is a combination of the right tools, practices, and staff training. Training should include all staff, regardless of role. It should be ongoing, perpetual, measurable, and delivered in various formats tailored to the specifics of your church staff.
11. Antivirus/endpoint protection
Implementing a robust, organization-wide antivirus solution on all Windows and macOS computers provides centralized reporting and advanced protections, including anti-malware, network protection, and content control capabilities. Enabling such a solution is a non-negotiable that strengthens your environment's security.
12. Vulnerability scanning
Identifying open weaknesses in your environment is critical to helping you know what you need to fix and protect. You should perform vulnerability scanning internally and externally and repeat it regularly to identify new threats. A good vulnerability scan will identify the systems with known problems that you can fix by installing appropriate patches, adjusting security parameters, or isolating the affected equipment so other network devices can't reach it.
13. Identity Threat Detection & Response
You can control access to your church’s most important data by carefully assigning appropriate access permissions to your trusted users. But what happens when an attacker takes over the digital identity of your user? Now your ‘trusted user’ is anything but trustworthy. So, it’s vitally important that you always protect the digital identity of your users. You need to know the minute a user’s online accounts are compromised and a “fox has entered the henhouse.” Ideally, if you believe someone’s account has been compromised, you will also want to immediately disable access to that account. This is exactly what an Identity Threat Detection and Response service does. They proactively monitor your online accounts and look for indicators of a compromised account. If they find suspicious activity, they can immediately disable access while notifying IT administrators so they can further investigate and remediate the threat.
14. Endpoint detection & response
A good cybersecurity defense program includes multiple layers of protection that work together to prevent, detect, and respond to attacks by malicious actors. Firewalls and traditional antivirus are great prevention layers, but it's essential to have other tools to detect and respond when cyber criminals successfully breach your preventative layers. Endpoint Detection and Response (EDR) or Managed Detection and Response (MDR) tools help cover the detect and respond phases by identifying threats that make it past your preventive defenses and providing steps to recover from a successful attack. You should install EDR tools on all servers and workstations.
15. Cybersecurity insurance
Cyber insurance, also called cyber risk insurance or cyber liability insurance, is a policy designed to help organizations mitigate risk exposure by offsetting costs involved with recovery after a cyber-related security breach or similar event. It covers scenarios generally not included in General Liability and Professional Liability policies. Given the environment in which they operate today, this is no longer optional for churches utilizing technology in ministry operations.
16. Backups/Business continuity
A robust ministry continuity plan involves the backup of data, systems, and servers. Such a plan ensures you back up data and machine images in geographically diverse sites. Your plan will allow you to avoid paying a "ransom" for your data and ensure you have good data backups. It will also provide for redundant capacity to continue the technology, reporting, data, and back-office ministry operations while you are recovering from any attack, incident, natural disaster, etc.
Download your copy of The Enable Cybersecurity Checklist below!